|

Special Announcement
Hello friends:
We are excited with the announcement of a new book now available written by Arkansas City,
Kansas author/artist Robert William Vincent (AKA) pabear48
Titled: Hray-Mah! The Earth
is Gone?
674 pages of reference for Serious Bible Study
Read
the Simplicity of the Gosple!
Learn what the Church's do not want you to read and know?
Like what are the SEVEN PRAYERS Jesus asked only those following him to pray?
Come and take a peek………. e-PDF instant downlaod $ 2.99
Click our safe link: HRAYMAH

Pabear's Computer Information is brought to you by
Annlee Cakes Native American Regalia and Crafts
408 East 5th Avenue
Arkansas City, Kansas 67005
Crafters of the Dance Circle jewelry and more.
Seed beaded earrings
Seed beaded Regalia necklace sets
Dancing and Circle style Items
Collectables and Antiques
Vintage Items
Art Originals and Art Prints
Arrowheads, rattles, and Dream Catchers
Native American Styled Hand Crafted Knifes
Peyote Stitch
and allot more.

***********************************************
PLEASE TAKE NOTE:
While I call it MALWARE ATTACKER:
It also is an “Embed Attacker Spy Ware”
Because it embeds itself into the Registry, and immediately
Shuts off system restore, fire walls and virus security.
From that initial hit: It drives itself deeper into your system
And no program has the ability as of January 20, 2011
To PREVENT OR STOP…..and none can remove once in!
THE ONLY THING: Stop…Do not move mouse!
Stop…Do not touch keyboard!
COLD BOOT DOWN YOUR SYSTEM
ASAP
Then follow my instructions: You should PRINT THEM
And have them at hand for they shall be needed sometime.
******************************************************************
This cave was created to aid in sharing HOW TO PROTECT YOUR COMPUTERS from the worst internet
malware attacker on the internet.
Anti Virus 2006, 2007, 2008, 2009,2010, 2011 and Best Virus and their newest one called Security
Tools.
Notice 2010: Now called THINK POINT
Usually you will get a POP UP...basically saying you are at risk or infected, or a security
scan is in progress:(matters not what it says)
You have been hit!
DO NOT EXPECT ANY POP UP BLOCKER TO STOP
THEM....they do not! Only you can save your system!
All "embed attacks" come from ONE SINGLE COMPANY!
All of the above are EXTREMELY BAD!
My desire in the following writing is to explain a bit about them and to show you THE
ONLY WAY and ONLY THING you can do to protect your entire system when their application hits your system as you surf
and explore the internet.
Please share what you read with family and friends.
Thank you,
pabear48
| I captured this one on January 20th 2011 |
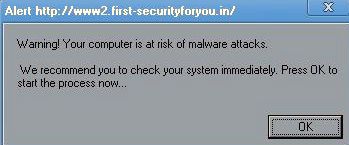
|
| This is a good example of what they llok like. |


|
| Click to visit Annlee Cakes Native Crafts |
The Internet grows and expands every single day. Your enjoyment and the safety for you and
your's now depends on knowledge you learn to protect your home system or even your laptop while surfing, exploring and enjoying
the entire Internet.
Sadly: There are people out there determined to extract your personal
information and if possible steal your identity or simply use methods trying to have you "buy" an item under the guise it
will protect you and your system.
It is true:
There are many virus's and trojons out there. Many companies that sell applications they say
will protect you and some free ones that say the same. Malware dos applications ARE NOT A VIRUS!
MALWARE:
Is the worst of all of them!
Mcafee, Nortons, Microsoft One Care, Microsoft Defender, Spy Bot and EVEN ALL POPUP
STOPPERS...
DO NOT STOP THE MALWARE EMBED ATTACKER
Anti Virus known now as THINK POINT AND OR
Best Virus is absolutely the worst attacker out there. And as of January 2001 they have started First "Securityforyou.in"
and IT WILL LITERALLY EAT YOUR SYSTEM piece by piece once it has installed itself in your working system. More bad people
are soon going to be using this same type attack application to infiltrate your systems. Only you can learn what to do and
share this with everyone that uses the computers at home or even at work because even firewalls cannot stop this unit because
when you go to a page or click any link from any search engine where they have attached this MALWARE....by clicking you yourself
grant permission for the link to open...Therefore YOU GRANTED permission for ALL THINGS ON THAT PAGE TO
ACTIVATE AS IT OPENS IN YOUR WINDOW.
You granted it administration rights to insert into the computers programming
system.
That is why and how it can appear!
YOU CAN STOP IT!
Details: THIS
IS THE ONLY KNOWN STOPPER METHOD!
If while your surfing or goggling and get hit when you click a link to a page by XPAntivirus2008 or 2009,
or Pro Version: or the newest BEST VIRUS, and NEW one called Alpha: 2010 also called now Security Tool: and their box opens
and appears on your screen: Security Tool has now been made worse in that if the new version hits you and locks
in it will stop SYSTEM RESTORE from working: Unless you bypass the applications working: READ BELOW!
Many have asked
what I would do and to share it!
First.....Do not click their box:
click no where: STOP
Instead STOP.......Simply restart your computer with the ON OFF BUTTON...doing
what is called a "COLD BOOT DOWN"......DO NOTHING ELSE except a cold boot down
ASAP
Your system will shut them down this way:
Upon restart:
Once on desktop. Go Control Panel. Internet Options. Open and clear out all caches (Internet Explorer): If using
other browsers....(make a short cut to its cleaning options in settings of the browser) then you can click that short cut
and clean the browser of choice you use (when needed).
Now use disc cleaner.....Restart........Now use disc cleaner
once more and use also the top option tab to use the system restore cleaner.....restart...once on desktop make a new restore
point saying like CLEANED MALWARE OUT.....restart.....that is it!
You are NOW clean and once more safe from this vicious
invader.
Hope this aids those who requested and others interested to be safe: Learning how to guard: That is exactly
what this writing is about and explaining how easy you can stop them properly so they do not get a registry entry: It
is important to learn this easy way! Why?
Because many more companies are getting ready for drop sale markers...Exactly
as this company has done...no law against them doing it......no program can stop their hitting you
if you bring up any site they have actively linked to auto set:
No program removes them! Not Mcafee/Not Nortons/not even
malware removal programs....not even Spybot!
ONLY YOU CAN PROTECT YOUR OWN SYSTEMS
It
is going to start happening more and more as others jump on this way of selling.
This method works on any invader...And
it makes your system safe after a hit.
IF YOU DID NOT STOP and accidently
did click anywhere?
There is one LAST DITCH EFFORT....(?)
If it is cought quickly!
There may be a way?
I will try explaining it fully step by step:
1.
Shut down the unit
2. Upon start up start tapping the F8 Key
3. When the target board appears: Use the arrow keys to
scroll to START IN SAFE MODE-without networking.
4. When your Main Page appears........go to System Restore.......choose
a restore point before the date of the attack.........highlight and restore.
5. When system restarts and returns to
main page....use Disc Clean up tool......Then make a NEW RESTORE POINT....Now use disc cleanup once more...and use this time
the top tab options...Bottom one should be clean out or clean up system restore points(these must be cleaned out because the
program is in there)......System will now clean itself.
6. Restart: It should automatically do its thing and bring
you back to desktop...and the attacker should be gone.
I know this can work for you !
We have saved many computers doing it this way before it attaches deeper into
the drives. If this does not work..because you may have clicked or moved the mouse granting them autorization to insert:
Then Factory Restore will accomplish the task 100 percent....but, the above explained is an option that works 99.99
percent of the time if we can catch it quick.
Pabear48
If my ideas "SAVED YOUR SYSTEM"
I ask of you just 2 things?
1. Share this web site with everyone you can!
They need the same information YOU FOUND
2. Visit our Online Store.....You do not need to buy ANYTHING
But, a simple visit helps our stores SEO Rankings
And, that is so very important ! Thank you..pabear


|
| Click me! I will take you to THE STORE |

We all need to protect our own systems until some company like say Microsoft does develope an application
which will hault embeded malware that by being attached to a page becomes activated and all install protocols granted simply
by clicking a link to view a page from a search engine suggestion.
Most users are simply unaware and uninformed in what to do, and WHY THEY MUST DO IT.
My goal here is explaining how they work and why they have permission to install upon your system, AND
HOW TO STOP THEM from installing!
I pray, all the above assists your fun and exploring upon the Internet with knowledge to save
your system when needed.
From
Wikipedia:
Malware, short for malicious
software, is software designed to infiltrate or damage a computer system without the owner's informed consent. The expression is a general term used by computer professionals to mean a variety of forms of hostile, intrusive, or annoying
software or program code.[1] The term "computer virus" is sometimes used as a catch-all phrase to include all types of malware, including true viruses.
Software is considered malware based on the perceived intent of the
creator rather than any particular features. Malware includes computer viruses, worms, trojan horses, most rootkits, spyware, dishonest adware, crimeware and other malicious and unwanted software. In law, malware is sometimes known as a computer contaminant, for instance in the legal codes of several U. S. states, including California and West Virginia


Thanks for visiting THE BEAR CAVE SYSTEM
Simply click my fishing bear to GO TO BEAR CONTROL SITE
Have fun, and happy surfing!

Brand New Bear Cave Shops
Jewelry Designed using the Art of
Arkansas City, Kansas artist/author
Robert William Vincent
Limited Editions some as low as 100 Worldwide to 500 WW
And many more items!
Visit this link:
Or this second Bear Shop:
And our third being updated:
Here is the total list of the ones I KNOW out there:
Each must attach via a POP UP BOX
You authorize them to INSTALL by any Mouse MOVE or any key touched on the Key Board:
Remember: COLD BOOT SHUT DOWN !!!!!!!!
THE LIST:
Smart Engine SecureDefense TrustDefender
ShieldSoldier IronProtector RegistryClever
IronDefense IronDefender Antivircat
SafetyGuard DesktopLayer HelpAssistant
Windows
Defence SpyDefender 2010 A-fast Antivirus Acommander
Active Security ActiveAntivir AdCare Advanced
Security Tool 2010 Advanced Virus Protection Adware Scanner 2010
AKM Antivirus 2010 Pro Alureon
AWM Antivirus
Anti virus Protection Anticare
AntiMalware / Anti Malware
Antispyware Defender
Antispyware Soft Antispyware Software
AntiSpyware Soldier Antivir / AnVi Antivir Solution Basic
Antivir Solution Pro Antivirus-1 / Anti-virus-1 Antivirus 7 /
Antivirus7 Antivirus 8 / Antivirus8 Antivirus 360
Antivirus 2009 Antivirus 2010 Antivirus 2010 / Antivirus2010
Antivirus 2010 Security Centre Antivirus Action / AntivirusAction
Antivirus GT Antivirus IS Antivirus Protection
AntiVirus Protector Antivirus Security Antivirus Soft
Antivirus Software Alert Antivirus Solution 2010 Antivirus
Studio 2010 Antivirus System Pro Antivirus XP
Antivirus XP Pro AV Antivirus Suite AV Checker
AVDefender 2011 AVScanner AV
Security Suite / antispybase.net AVSecuirtySuite ByteDefender
Cleanup Antivirus / Clean up Antivirus Contraviro Control Center
ControlCnt CoreGuard CTRLComponents Data
Protection DeadEye / Dead Eye Defence Lab
Defense Center / DefenseCenter Defender Pro Desktop
Security 2010 Desktop Security 2010 Digital Protection
Dr. Guard drive cleaner Earth Antivirus / Earth AV”
ErrorWiz Extreme Security 2010 EzPrivacy
Gala Search Green AV Security Suite GreenVaccine
Hardclean Inprivacy Internet Antivirus
Pro Internet Security 2010 IP Clear
IronProtector / Iron Protector ShieldSoldier Live
Security Suite Malware Destructor 2009 Malware Destructor
2011
MalwareDestructor2011 Malware Doctor
MalwareDoc My Computer Online Scan My Security Engine
My Security Shield MyClean MyFasterComputer
NavaShield Net Protector AntiVirus 2010NetworkControl / Network
Control OneClean OneScan PC
Defender PC Defender Antivirus PC Sweeper
PC-Guide Pcenter PCommander Personal Anti
Malware Center Personal Antivirus Personal Security
Privacy Center ProtectInfo Protection Center
/ ProtectionCenter Protection System RegClean
Registry Doctor Registry Smart Pro ResetInfo
SafetyPC Sahat SecureDefense / Secure
DefenseSecurity 2009 Security 2009 Security
Hijack Security Master AV Security Suite / SecuritySuite
Security Suite Pro Security Tool / SecurityTool ShieldSoldier
/ Shield Soldier SmartSecurity / XP Smart Security SP Center
Spy Cleaner SpyAway Spycheck AntiSpyware / Spycheck
Anti-Spyware 2010 SpyGuard Spyware Cleaner 2010 Spyware
Protect SpywareVanisher / Spyware Vanisher SysGuardSysinternals
Antivirus System Antivirus 2008 System Defragmenter System
Security System Security 2009 SystemArmor SystemArmor
ThinkPoint Total PC Defender Total Security
TrustDefender / Trust Defender TrustDoctor UnVirex
User Account Control User Protection VaccineCenter
VaccineData
VaccineTree Vdoctor Virus Doctor Virus
Protector Virus Remover Virus Remover 2009
Virus Remover Professional Virus Total 2010 VirusCatch
VirusCure VSCAN7 VSCodec Pro Trojan Win
Antispyware Center Win Center WinBlueSoft WinCleaner
Wind Optimizer WinPC Defender / Win PC Defender / Win PC Antivirus
Win7 AV Wireshark Antivirus XP Deluxe Protector Your
PC Protector Your Protection Tango toolbar ResultDNS
THINK
POINT is the newest right now !


Microsoft’s Malicious Software Removal Tool.
This is a great and safe application to learn How to Use.
We have all seen Microsoft Update installing updates for this
Tool to use in finding and correcting problems from bad apps.
The problem my friends is few know How to Use it?
To activate the unit:
Click on your start button icon.
Then click the RUN tab
Now type in the box: MRT.EXE
The application unit will now open up.
Click NEXT
You have choices: Quick scan…Full Scan…Customized scan
Normally all you will ever use is the QUICK SCAN
But, once every month Run the FULL SCAN just before you head to bed because it takes a
very long time and will be sitting there done in
the morning.
RUN THE SCAN……..If it finds anything simply follow it’s suggestions and
directions. If not close and enjoy your system.
IF it did find things…Remember after a restart…MAKE A RESTORE POINT….and
then clean out all OLD RESTORE POINTS
MRT.EXE is worth the effort to learn How to
Use !
Blessings…….pabear48
REMEMBER this unit while good for many items DOES NOT ADDRESS MALWARE EMBEDED SPYWARE ATTACKS.
And, cannot remove then or stop then once it has activated with your permissions to insert simply because
you wanted to view a web page you searched for and your browser opened the page and the "Embed was there".

If you would like to:
You may make a donation helping to keep this site active.
And able to aid all computer users.
The choice is 100 percent yours !
Did this page fix your system? Protect it ?
Now ask yourself: "How much you saved because it's here?"
Either way.......Thank you..........pabear48

|
| Click this picture to visit: Annlee cakes Native American Crafts |
|

